Page 131 - StudyBook.pdf
P. 131
Communication Security: Remote Access and Messaging • Chapter 3 115
Site-to-site VPN
Site-to-site VPNs are normally established between corporate offices that are sepa-
rated by a physical distance extending further than normal campus area.VPNs are
available in software (such as the Windows VPN available on Windows Server 2003
RRAS Server and Microsoft ISA 2006 Firewall) and hardware (firewalls such as
Nokia/Checkpoint and Cisco’s PIX and ASA) implementations. It had been a gen-
eral understanding that software implementations are easier to maintain, mostly due
to the familiar graphical user interface (GUI). However, manufacturers of hard-
ware-based solutions have gone to great lengths to provide more usable interfaces,
and since hardware implementations have always been considered more secure
(they are not impacted by OS vulnerabilities), there has been a rise in the calling
for security professionals to have a working knowledge of both hardware and soft-
ware solutions.
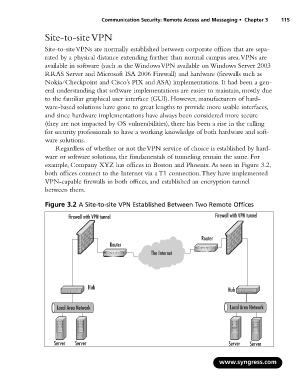
Regardless of whether or not the VPN service of choice is established by hard-
ware or software solutions, the fundamentals of tunneling remain the same. For
example, Company XYZ has offices in Boston and Phoenix.As seen in Figure 3.2,
both offices connect to the Internet via a T1 connection.They have implemented
VPN-capable firewalls in both offices, and established an encryption tunnel
between them.
Figure 3.2 A Site-to-site VPN Established Between Two Remote Offices
Firewall with VPN tunnel Firewall with VPN tunnel
Router
Router
The Internet
Hub Hub
Local Area Network Local Area Network
Server Server Server Server
www.syngress.com