Page 203 - StudyBook.pdf
P. 203
Communication Security: Wireless • Chapter 4 187
EXAM WARNING
Open authentication can also require the use of a WEP key. Do not
assume that just because the Security+ exam discusses open authentica-
tion that a WEP key should not be set.
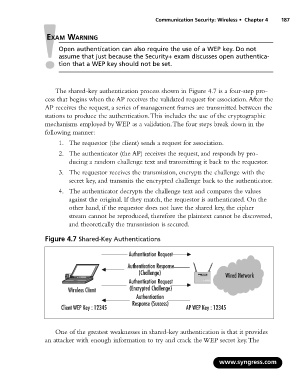
The shared-key authentication process shown in Figure 4.7 is a four-step pro-
cess that begins when the AP receives the validated request for association.After the
AP receives the request, a series of management frames are transmitted between the
stations to produce the authentication.This includes the use of the cryptographic
mechanisms employed by WEP as a validation.The four steps break down in the
following manner:
1. The requestor (the client) sends a request for association.
2. The authenticator (the AP) receives the request, and responds by pro-
ducing a random challenge text and transmitting it back to the requestor.
3. The requestor receives the transmission, encrypts the challenge with the
secret key, and transmits the encrypted challenge back to the authenticator.
4. The authenticator decrypts the challenge text and compares the values
against the original. If they match, the requestor is authenticated. On the
other hand, if the requestor does not have the shared key, the cipher
stream cannot be reproduced, therefore the plaintext cannot be discovered,
and theoretically the transmission is secured.
Figure 4.7 Shared-Key Authentications
Authentication Request
Authentication Response
(Challenge) Wired Network
Authentication Request
Wireless Client (Encrypted Challenge)
Authentication
Response (Success)
Client WEP Key : 12345 AP WEP Key : 12345
One of the greatest weaknesses in shared-key authentication is that it provides
an attacker with enough information to try and crack the WEP secret key.The
www.syngress.com