Page 79 - StudyBook.pdf
P. 79
General Security Concepts: Attacks • Chapter 2 63
zombies. Masters receive orders that they then trickle through to the zombies for
which they are responsible.The master is only responsible for sending and receiving
short control messages, making lower bandwidth networks just as suitable as higher
bandwidth networks.
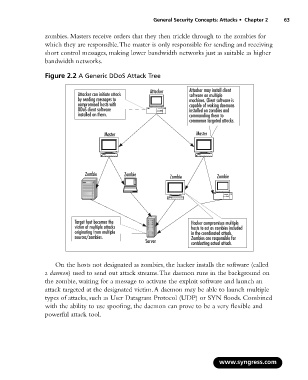
Figure 2.2 A Generic DDoS Attack Tree
Attacker Attacker may install client
Attacker can initiate attack software on multiple
by sending messages to machines. Client software is
compromised hosts with capable of waking daemons
DDoS client software installed on zombies and
installed on them. commanding them to
commence targeted attacks.
Master Master
Zombie Zombie Zombie Zombie
Target host becomes the Hacker compromises multiple
victim of multiple attacks hosts to act as zombies included
originating from multiple in the coordinated attack.
sources/zombies. Zombies are responsible for
Server contducting actual attack.
On the hosts not designated as zombies, the hacker installs the software (called
a daemon) used to send out attack streams.The daemon runs in the background on
the zombie, waiting for a message to activate the exploit software and launch an
attack targeted at the designated victim.A daemon may be able to launch multiple
types of attacks, such as User Datagram Protocol (UDP) or SYN floods. Combined
with the ability to use spoofing, the daemon can prove to be a very flexible and
powerful attack tool.
www.syngress.com