Page 21 - info_oct_2021_draft13
P. 21
In Focus
ModSecurity Phase:1
Request Headers
URI Translation Access Control
Post-Read-Request Header Parsing Authentication
Wait Authorization
Cleanup MIME type checking
Logging Fixups
ModSecurity Phase:5 Response ModSecurity Phase:2
Logging Request Body
ModSecurity Phase:4 ModSecurity Phase:3
Response Body Response Headers
ModSecurity Transaction Phases
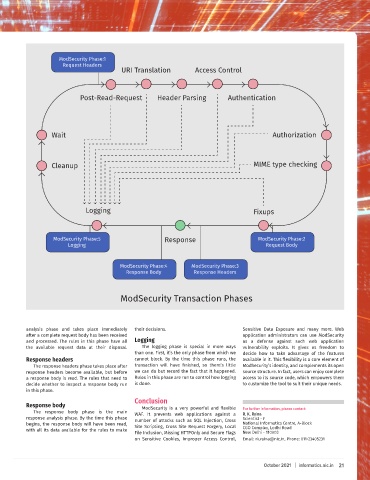
analysis phase and takes place immediately their decisions. Sensitive Data Exposure and many more. Web
after a complete request body has been received application administrators can use ModSecurity
and processed. The rules in this phase have all Logging as a defense against such web application
the available request data at their disposal. The logging phase is special in more ways vulnerability exploits. It gives us freedom to
than one. First, it’s the only phase from which we decide how to take advantage of the features
Response headers cannot block. By the time this phase runs, the available in it. This flexibility is a core element of
The response headers phase takes place after transaction will have finished, so there’s little ModSecurity’s identity, and complements its open
response headers become available, but before we can do but record the fact that it happened. source structure. In fact, users can enjoy complete
a response body is read. The rules that need to Rules in this phase are run to control how logging access to its source code, which empowers them
decide whether to inspect a response body run is done. to customize the tool to suit their unique needs.
in this phase.
Conclusion
Response body ModSecurity is a very powerful and flexible
The response body phase is the main WAF. It prevents web applications against a For further information, please contact:
response analysis phase. By the time this phase number of attacks such as SQL Injection, Cross R. K. Raina
Scientist - F
begins, the response body will have been read, Site Scripting, Cross Site Request Forgery, Local National Informatics Centre, A-Block
with all its data available for the rules to make File Inclusion, Missing HTTPOnly and Secure Flags CGO Complex, Lodhi Road
New Delhi - 110003
on Sensitive Cookies, Improper Access Control, Email: rk.raina@nic.in, Phone: 011-23405231
informatics.nic.in 21
October 2021 informatics.nic.in 21
October 2021