Page 25 - ITGC_Audit Guides
P. 25
Messages are consumed using one of two queuing protocols: Post Office Protocol (POP) and
Internet Message Access Protocol (IMAP):
POP messages are received and stored on an email server. When these messages are
consumed, they are downloaded to the consumer’s device. Messages are not retained on the
server once consumed.
IMAP messages are received and retained on an email server. When these messages are
consumed, they can be organized into various folders rather than being downloaded to the
consumer’s device. Messages are retained on the server once consumed, thus IMAP can be
thought of as a file server for messages.
Email Domains and Participants
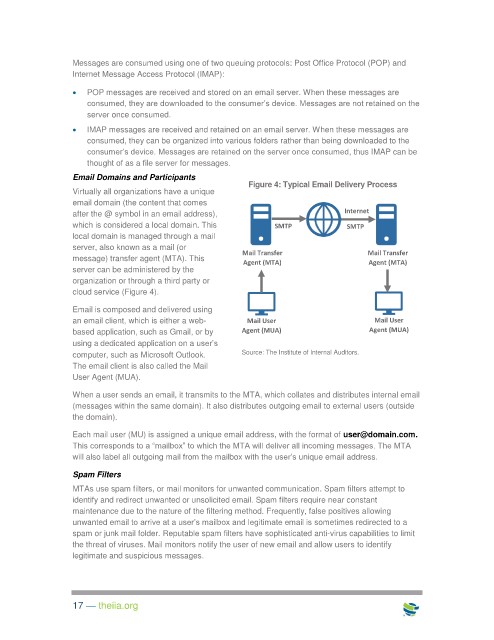
Figure 4: Typical Email Delivery Process
Virtually all organizations have a unique
email domain (the content that comes
after the @ symbol in an email address), Internet
which is considered a local domain. This SMTP SMTP
local domain is managed through a mail
server, also known as a mail (or
Mail Transfer Mail Transfer
message) transfer agent (MTA). This
Agent (MTA) Agent (MTA)
server can be administered by the
organization or through a third party or
cloud service (Figure 4).
Email is composed and delivered using
an email client, which is either a web- Mail User Mail User
based application, such as Gmail, or by Agent (MUA) Agent (MUA)
using a dedicated application on a user’s
computer, such as Microsoft Outlook. Source: The Institute of Internal Auditors.
The email client is also called the Mail
User Agent (MUA).
When a user sends an email, it transmits to the MTA, which collates and distributes internal email
(messages within the same domain). It also distributes outgoing email to external users (outside
the domain).
Each mail user (MU) is assigned a unique email address, with the format of user@domain.com.
This corresponds to a “mailbox” to which the MTA will deliver all incoming messages. The MTA
will also label all outgoing mail from the mailbox with the user’s unique email address.
Spam Filters
MTAs use spam filters, or mail monitors for unwanted communication. Spam filters attempt to
identify and redirect unwanted or unsolicited email. Spam filters require near constant
maintenance due to the nature of the filtering method. Frequently, false positives allowing
unwanted email to arrive at a user’s mailbox and legitimate email is sometimes redirected to a
spam or junk mail folder. Reputable spam filters have sophisticated anti-virus capabilities to limit
the threat of viruses. Mail monitors notify the user of new email and allow users to identify
legitimate and suspicious messages.
17 — theiia.org