Page 26 - ITGC_Audit Guides
P. 26
File Sharing
Before the internet and networked devices, users would share files using floppy disks. With the
advent of protocols such as File Transfer Protocol (FTP) and Secure File Transfer Protocol
(SFTP) (mentioned in the Protocols portion of the IT Network section), file sharing became easier,
but not necessarily user friendly. File sharing allows users to easily share files such as books,
music, photos, or anything in an electronic format, either publicly or privately, over the internet
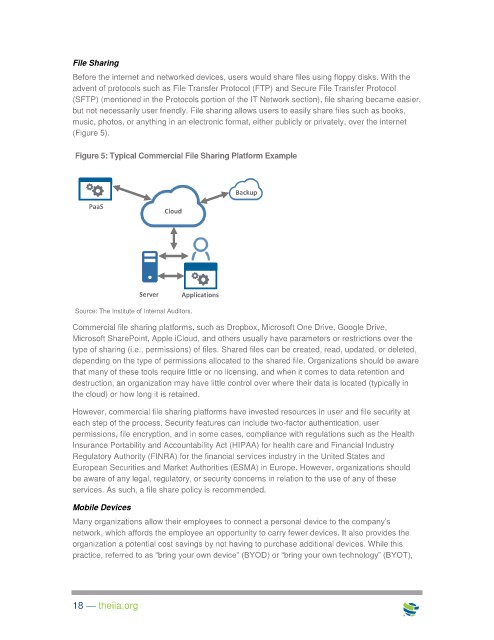
(Figure 5).
Figure 5: Typical Commercial File Sharing Platform Example
Backup
PaaS
Cloud
Server Applications
Source: The Institute of Internal Auditors.
Commercial file sharing platforms, such as Dropbox, Microsoft One Drive, Google Drive,
Microsoft SharePoint, Apple iCloud, and others usually have parameters or restrictions over the
type of sharing (i.e., permissions) of files. Shared files can be created, read, updated, or deleted,
depending on the type of permissions allocated to the shared file. Organizations should be aware
that many of these tools require little or no licensing, and when it comes to data retention and
destruction, an organization may have little control over where their data is located (typically in
the cloud) or how long it is retained.
However, commercial file sharing platforms have invested resources in user and file security at
each step of the process. Security features can include two-factor authentication, user
permissions, file encryption, and in some cases, compliance with regulations such as the Health
Insurance Portability and Accountability Act (HIPAA) for health care and Financial Industry
Regulatory Authority (FINRA) for the financial services industry in the United States and
European Securities and Market Authorities (ESMA) in Europe. However, organizations should
be aware of any legal, regulatory, or security concerns in relation to the use of any of these
services. As such, a file share policy is recommended.
Mobile Devices
Many organizations allow their employees to connect a personal device to the company’s
network, which affords the employee an opportunity to carry fewer devices. It also provides the
organization a potential cost savings by not having to purchase additional devices. While this
practice, referred to as “bring your own device” (BYOD) or “bring your own technology” (BYOT),
18 — theiia.org