Page 447 - From GMS to LTE
P. 447
Wireless Local Area Network (WLAN) 433
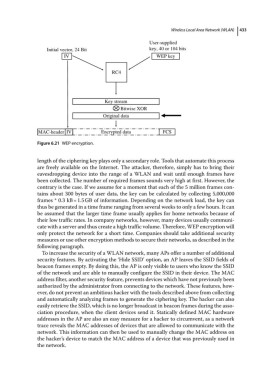
User-supplied
Initial vector, 24 Bit key, 40 or 104 bits
IV WEP key
RC4
Key stream
Bitwise XOR
Original data
MAC-header IV Encrypted data FCS
Figure 6.21 WEP encryption.
length of the ciphering key plays only a secondary role. Tools that automate this process
are freely available on the Internet. The attacker, therefore, simply has to bring their
eavesdropping device into the range of a WLAN and wait until enough frames have
been collected. The number of required frames sounds very high at first. However, the
contrary is the case. If we assume for a moment that each of the 5 million frames con-
tains about 300 bytes of user data, the key can be calculated by collecting 5,000,000
frames * 0.3 kB = 1.5 GB of information. Depending on the network load, the key can
thus be generated in a time frame ranging from several weeks to only a few hours. It can
be assumed that the larger time frame usually applies for home networks because of
their low traffic rates. In company networks, however, many devices usually communi-
cate with a server and thus create a high traffic volume. Therefore, WEP encryption will
only protect the network for a short time. Companies should take additional security
measures or use other encryption methods to secure their networks, as described in the
following paragraph.
To increase the security of a WLAN network, many APs offer a number of additional
security features. By activating the ‘Hide SSID’ option, an AP leaves the SSID fields of
beacon frames empty. By doing this, the AP is only visible to users who know the SSID
of the network and are able to manually configure the SSID in their device. The MAC
address filter, another security feature, prevents devices which have not previously been
authorized by the administrator from connecting to the network. These features, how-
ever, do not prevent an ambitious hacker with the tools described above from collecting
and automatically analyzing frames to generate the ciphering key. The hacker can also
easily retrieve the SSID, which is no longer broadcast in beacon frames during the asso-
ciation procedure, when the client devices send it. Statically defined MAC hardware
addresses in the AP are also an easy measure for a hacker to circumvent, as a network
trace reveals the MAC addresses of devices that are allowed to communicate with the
network. This information can then be used to manually change the MAC address on
the hacker’s device to match the MAC address of a device that was previously used in
the network.