Page 490 - From GMS to LTE
P. 490
476 From GSM to LTE-Advanced Pro and 5G
Dial up OBEX … SDP database Application X …
Multiplexing of
applications that
RFCOMM are based on
serial interfaces
Multiplexing of
L2CAP different data
… streams per device
ACL frames ACL frames
for device 1 for device 2
Multiplexing of data
HCI layer frames for several
devices
ACL frames of several devices
Bluetooth controller chip
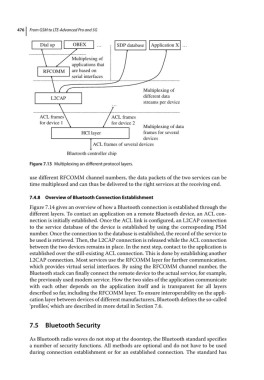
Figure 7.13 Multiplexing on different protocol layers.
use different RFCOMM channel numbers, the data packets of the two services can be
time multiplexed and can thus be delivered to the right services at the receiving end.
7.4.8 Overview of Bluetooth Connection Establishment
Figure 7.14 gives an overview of how a Bluetooth connection is established through the
different layers. To contact an application on a remote Bluetooth device, an ACL con-
nection is initially established. Once the ACL link is configured, an L2CAP connection
to the service database of the device is established by using the corresponding PSM
number. Once the connection to the database is established, the record of the service to
be used is retrieved. Then, the L2CAP connection is released while the ACL connection
between the two devices remains in place. In the next step, contact to the application is
established over the still‐existing ACL connection. This is done by establishing another
L2CAP connection. Most services use the RFCOMM layer for further communication,
which provides virtual serial interfaces. By using the RFCOMM channel number, the
Bluetooth stack can finally connect the remote device to the actual service, for example,
the previously used modem service. How the two sides of the application communicate
with each other depends on the application itself and is transparent for all layers
described so far, including the RFCOMM layer. To ensure interoperability on the appli-
cation layer between devices of different manufacturers, Bluetooth defines the so‐called
‘profiles’, which are described in more detail in Section 7.6.
7.5 Bluetooth Security
As Bluetooth radio waves do not stop at the doorstep, the Bluetooth standard specifies
a number of security functions. All methods are optional and do not have to be used
during connection establishment or for an established connection. The standard has