Page 495 - From GMS to LTE
P. 495
Bluetooth and Bluetooth Low Energy 481
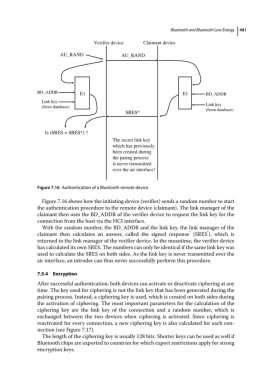
Verifier device Claimant device
AU_RAND AU_RAND
BD_ADDR E1 E1 BD_ADDR
Link key
(from database) Link key
SRES* (from database)
Is (SRES = SRES*) ?
The secret link key
which has previously
been created during
the paring process
is never transmitted
over the air interface!
Figure 7.16 Authentication of a Bluetooth remote device.
Figure 7.16 shows how the initiating device (verifier) sends a random number to start
the authentication procedure to the remote device (claimant). The link manager of the
claimant then uses the BD_ADDR of the verifier device to request the link key for the
connection from the host via the HCI interface.
With the random number, the BD_ADDR and the link key, the link manager of the
*
*
claimant then calculates an answer, called the signed response (SRES ), which is
returned to the link manager of the verifier device. In the meantime, the verifier device
has calculated its own SRES. The numbers can only be identical if the same link key was
used to calculate the SRES on both sides. As the link key is never transmitted over the
air interface, an intruder can thus never successfully perform this procedure.
7.5.4 Encryption
After successful authentication, both devices can activate or deactivate ciphering at any
time. The key used for ciphering is not the link key that has been generated during the
pairing process. Instead, a ciphering key is used, which is created on both sides during
the activation of ciphering. The most important parameters for the calculation of the
ciphering key are the link key of the connection and a random number, which is
exchanged between the two devices when ciphering is activated. Since ciphering is
reactivated for every connection, a new ciphering key is also calculated for each con-
nection (see Figure 7.17).
The length of the ciphering key is usually 128 bits. Shorter keys can be used as well if
Bluetooth chips are exported to countries for which export restrictions apply for strong
encryption keys.