Page 496 - From GMS to LTE
P. 496
482 From GSM to LTE-Advanced Pro and 5G
Air interface
Device A Device B
BD_ADDR (A) BD_ADDR (A)
Clock (A) E0 E0 Clock (A)
K c K c
K cipher K cipher
Original data streams Ciphered data streams Original data streams
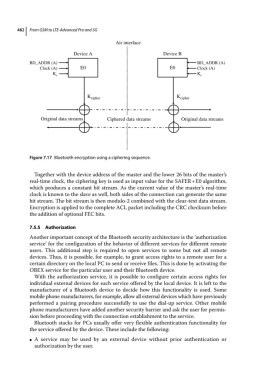
Figure 7.17 Bluetooth encryption using a ciphering sequence.
Together with the device address of the master and the lower 26 bits of the master’s
real‐time clock, the ciphering key is used as input value for the SAFER + E0 algorithm,
which produces a constant bit stream. As the current value of the master’s real‐time
clock is known to the slave as well, both sides of the connection can generate the same
bit stream. The bit stream is then modulo‐2 combined with the clear‐text data stream.
Encryption is applied to the complete ACL packet including the CRC checksum before
the addition of optional FEC bits.
7.5.5 Authorization
Another important concept of the Bluetooth security architecture is the ‘authorization
service’ for the configuration of the behavior of different services for different remote
users. This additional step is required to open services to some but not all remote
devices. Thus, it is possible, for example, to grant access rights to a remote user for a
certain directory on the local PC to send or receive files. This is done by activating the
OBEX service for the particular user and their Bluetooth device.
With the authorization service, it is possible to configure certain access rights for
individual external devices for each service offered by the local device. It is left to the
manufacturer of a Bluetooth device to decide how this functionality is used. Some
mobile phone manufacturers, for example, allow all external devices which have previously
performed a pairing procedure successfully to use the dial‐up service. Other mobile
phone manufacturers have added another security barrier and ask the user for permis-
sion before proceeding with the connection establishment to the service.
Bluetooth stacks for PCs usually offer very flexible authentication functionality for
the service offered by the device. These include the following:
A service may be used by an external device without prior authentication or
●
authorization by the user.