Page 491 - From GMS to LTE
P. 491
Bluetooth and Bluetooth Low Energy 477
RFCOMM ACL-link
Application L2CAP
Service
Remote Bluetooth device
database
t
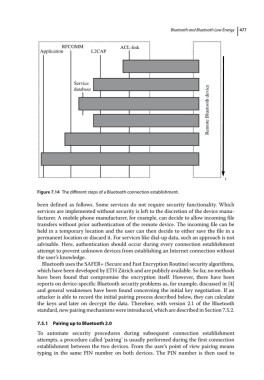
Figure 7.14 The different steps of a Bluetooth connection establishment.
been defined as follows. Some services do not require security functionality. Which
services are implemented without security is left to the discretion of the device manu-
facturer. A mobile phone manufacturer, for example, can decide to allow incoming file
transfers without prior authentication of the remote device. The incoming file can be
held in a temporary location and the user can then decide to either save the file in a
permanent location or discard it. For services like dial‐up data, such an approach is not
advisable. Here, authentication should occur during every connection establishment
attempt to prevent unknown devices from establishing an Internet connection without
the user’s knowledge.
Bluetooth uses the SAFER+ (Secure and Fast Encryption Routine) security algorithms,
which have been developed by ETH Zürich and are publicly available. So far, no methods
have been found that compromise the encryption itself. However, there have been
reports on device‐specific Bluetooth security problems as, for example, discussed in [4]
and general weaknesses have been found concerning the initial key negotiation. If an
attacker is able to record the initial pairing process described below, they can calculate
the keys and later on decrypt the data. Therefore, with version 2.1 of the Bluetooth
standard, new pairing mechanisms were introduced, which are described in Section 7.5.2.
7.5.1 Pairing up to Bluetooth 2.0
To automate security procedures during subsequent connection establishment
attempts, a procedure called ‘pairing’ is usually performed during the first connection
establishment between the two devices. From the user’s point of view pairing means
typing in the same PIN number on both devices. The PIN number is then used to