Page 473 - BSIT Course Syllabus (First Sem 2020-2021)
P. 473
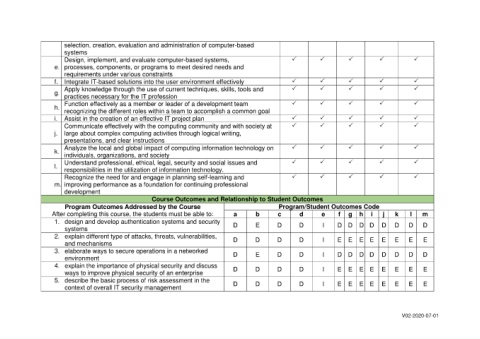
selection, creation, evaluation and administration of computer-based
systems
Design, implement, and evaluate computer-based systems,
e. processes, components, or programs to meet desired needs and
requirements under various constraints
f. ntegrate IT-based solutions into the user environment effectively
I
Apply knowledge through the use of current techniques, skills, tools and
g.
practices necessary for the IT profession
Function effectively as a member or leader of a development team
h.
recognizing the different roles within a team to accomplish a common goal
i. Assist in the creation of an effective IT project plan
Communicate effectively with the computing community and with society at
l
j. arge about complex computing activities through logical writing,
presentations, and clear instructions
Analyze the local and global impact of computing information technology on
k.
individuals, organizations, and society
Understand professional, ethical, legal, security and social issues and
l.
responsibilities in the utilization of information technology.
Recognize the need for and engage in planning self-learning and
m. mproving performance as a foundation for continuing professional
i
development
Course Outcomes and Relationship to Student Outcomes
Program Outcomes Addressed by the Course Program/Student Outcomes Code
After completing this course, the students must be able to: a b c d e f g h i j k l m
1. design and develop authentication systems and security D E D D I D D D D D D D D
systems
2. explain different type of attacks, threats, vulnerabilities, D D D D I E E E E E E E E
and mechanisms
3. elaborate ways to secure operations in a networked D E D D I D D D D D D D D
environment
4. explain the importance of physical security and discuss
ways to improve physical security of an enterprise D D D D I E E E E E E E E
5. describe the basic process of risk assessment in the
context of overall IT security management D D D D I E E E E E E E E
V02-2020-07-01