Page 475 - BSIT Course Syllabus (First Sem 2020-2021)
P. 475
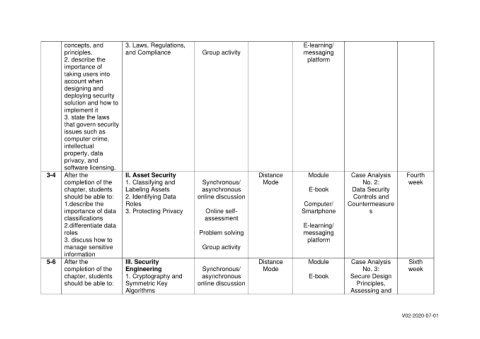
concepts, and 3. Laws, Regulations, E-learning/
principles. and Compliance Group activity messaging
2. describe the platform
importance of
taking users into
account when
designing and
deploying security
solution and how to
implement it
3. state the laws
that govern security
issues such as
computer crime,
intellectual
property, data
privacy, and
software licensing.
3-4 After the II. Asset Security Distance Module Case Analysis Fourth
completion of the 1. Classifying and Synchronous/ Mode No. 2: week
chapter, students Labeling Assets asynchronous E-book Data Security
should be able to: 2. Identifying Data online discussion Controls and
1.describe the Roles Computer/ Countermeasure
importance of data 3. Protecting Privacy Online self- Smartphone s
classifications assessment
2.differentiate data E-learning/
roles Problem solving messaging
3. discuss how to platform
manage sensitive Group activity
information
5-6 After the III. Security Distance Module Case Analysis Sixth
completion of the Engineering Synchronous/ Mode No. 3: week
chapter, students 1. Cryptography and asynchronous E-book Secure Design
should be able to: Symmetric Key online discussion Principles,
Algorithms Assessing and
V02-2020-07-01