Page 468 - StudyBook.pdf
P. 468
452 Chapter 7 • Topologies and IDS
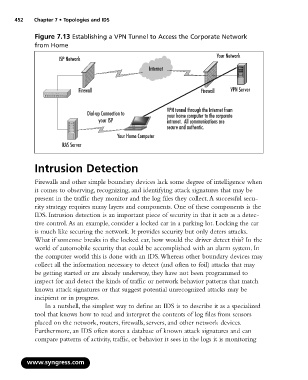
Figure 7.13 Establishing a VPN Tunnel to Access the Corporate Network
from Home
Your Network
ISP Network
Internet
Firewall Firewall VPN Server
VPN tunnel through the Internet from
Dial-up Connection to your home computer to the corporate
your ISP intranet. All communications are
secure and authentic.
Your Home Computer
RAS Server
Intrusion Detection
Firewalls and other simple boundary devices lack some degree of intelligence when
it comes to observing, recognizing, and identifying attack signatures that may be
present in the traffic they monitor and the log files they collect.A successful secu-
rity strategy requires many layers and components. One of these components is the
IDS. Intrusion detection is an important piece of security in that it acts as a detec-
tive control.As an example, consider a locked car in a parking lot. Locking the car
is much like securing the network. It provides security but only deters attacks.
What if someone breaks in the locked car, how would the driver detect this? In the
world of automobile security that could be accomplished with an alarm system. In
the computer world this is done with an IDS.Whereas other boundary devices may
collect all the information necessary to detect (and often to foil) attacks that may
be getting started or are already underway, they have not been programmed to
inspect for and detect the kinds of traffic or network behavior patterns that match
known attack signatures or that suggest potential unrecognized attacks may be
incipient or in progress.
In a nutshell, the simplest way to define an IDS is to describe it as a specialized
tool that knows how to read and interpret the contents of log files from sensors
placed on the network, routers, firewalls, servers, and other network devices.
Furthermore, an IDS often stores a database of known attack signatures and can
compare patterns of activity, traffic, or behavior it sees in the logs it is monitoring
www.syngress.com