Page 467 - StudyBook.pdf
P. 467
Topologies and IDS • Chapter 7 451
EXAM WARNING
Tunneling is used in conjunction with encryption to provide total end-
to-end data protection across an untrustworthy network, such as the
Internet. Point-to-Point Tunneling Protocol (PPTP) and Layer 2 Tunneling
Protocol (L2TP) are popular VPN tunneling protocols, while Microsoft
Point-to-Point Encryption (MPPE) and IPSec are their encryption counter-
parts. Do not confuse tunneling with encryption.
VPN tunneling provides confidentiality of data, in that the traffic is encrypted,
typically using MPPE or IPSec.VPNs created using the L2TP use IPSec for
encryption, whereas tunnels created with the PPTP use MPPE.Windows XP and
newer Microsoft OSes can use IPSec; all older versions must use MPPE.
Most other new OSes also provide support for L2TP and IPSec.Tunnels can
also be created using IPSec alone (without L2TP) or using Secure Shell (SSH) or
Crypto Internet Protocol Encapsulation (CIPE) in Linux/UNIX environments. It
is important to understand that tunneling and encryption are two separate pro-
cesses, both of which are necessary to create a VPN.
For more information about VPN technologies, see http://en.wikipedia.
org/wiki/VPN.Tunneling is often used when configuring and implementing an
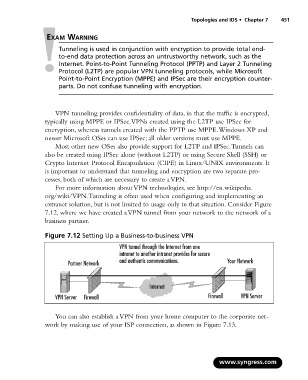
extranet solution, but is not limited to usage only in that situation. Consider Figure
7.12, where we have created a VPN tunnel from your network to the network of a
business partner.
Figure 7.12 Setting Up a Business-to-business VPN
VPN tunnel through the Internet from one
intranet to another intranet provides for secure
Partner Network and authentic communications. Your Network
Internet
VPN Server Firewall Firewall VPN Server
You can also establish a VPN from your home computer to the corporate net-
work by making use of your ISP connection, as shown in Figure 7.13.
www.syngress.com