Page 385 - ITGC_Audit Guides
P. 385
Review access control lists and firewall restrictions that limit access to sensitive systems
and data located on the internal network.
Identify and review applicable laws and
regulations that influence the context of
Audit Considerations
the audit engagement.
CERT’s list of 20 practices included in
Interviewing Relevant Stakeholders Appendix D may be used to develop
To gather information, internal auditors may internal control questionnaires (ICQs)
interview employees who perform tasks associated to gather information about control
with the insider threat program, the management activities during the engagement
responsible for oversight, and the individuals with planning phase, or to develop
authority to make decisions. Some of the stakeholder interview questions.
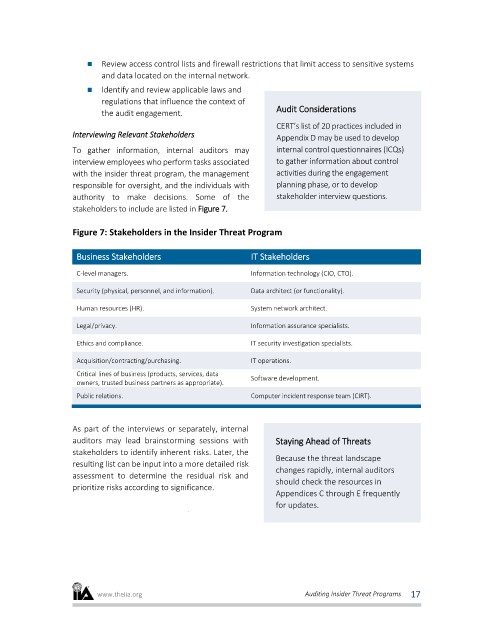
stakeholders to include are listed in Figure 7.
Figure 7: Stakeholders in the Insider Threat Program
Business Stakeholders IT Stakeholders
C-level managers. Information technology (CIO, CTO).
Security (physical, personnel, and information). Data architect (or functionality).
Human resources (HR). System network architect.
Legal/privacy. Information assurance specialists.
Ethics and compliance. IT security investigation specialists.
Acquisition/contracting/purchasing. IT operations.
Critical lines of business (products, services, data
Software development.
owners, trusted business partners as appropriate).
Public relations. Computer incident response team (CIRT).
As part of the interviews or separately, internal
auditors may lead brainstorming sessions with Staying Ahead of Threats
stakeholders to identify inherent risks. Later, the
Because the threat landscape
resulting list can be input into a more detailed risk
changes rapidly, internal auditors
assessment to determine the residual risk and
should check the resources in
prioritize risks according to significance.
Appendices C through E frequently
for updates.
www.theiia.org Auditing Insider Threat Programs 17