Page 387 - ITGC_Audit Guides
P. 387
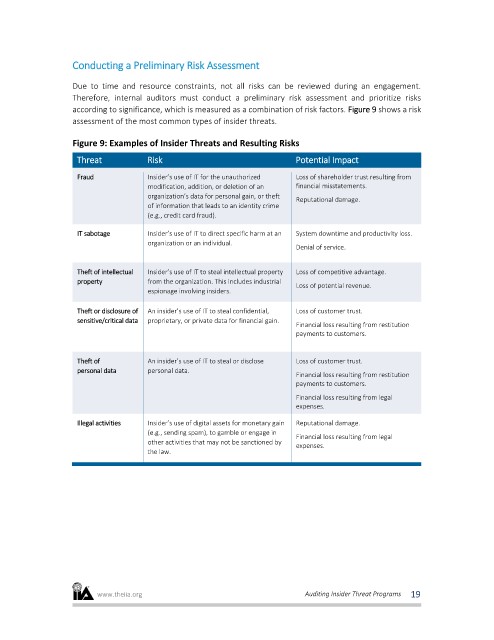
Conducting a Preliminary Risk Assessment
Due to time and resource constraints, not all risks can be reviewed during an engagement.
Therefore, internal auditors must conduct a preliminary risk assessment and prioritize risks
according to significance, which is measured as a combination of risk factors. Figure 9 shows a risk
assessment of the most common types of insider threats.
Figure 9: Examples of Insider Threats and Resulting Risks
Threat Risk Potential Impact
Fraud Insider’s use of IT for the unauthorized Loss of shareholder trust resulting from
modification, addition, or deletion of an financial misstatements.
organization’s data for personal gain, or theft
Reputational damage.
of information that leads to an identity crime
(e.g., credit card fraud).
IT sabotage Insider’s use of IT to direct specific harm at an System downtime and productivity loss.
organization or an individual.
Denial of service.
Theft of intellectual Insider’s use of IT to steal intellectual property Loss of competitive advantage.
property from the organization. This includes industrial
Loss of potential revenue.
espionage involving insiders.
Theft or disclosure of An insider’s use of IT to steal confidential, Loss of customer trust.
sensitive/critical data proprietary, or private data for financial gain.
Financial loss resulting from restitution
payments to customers.
Theft of An insider’s use of IT to steal or disclose Loss of customer trust.
personal data personal data.
Financial loss resulting from restitution
payments to customers.
Financial loss resulting from legal
expenses.
Illegal activities Insider’s use of digital assets for monetary gain Reputational damage.
(e.g., sending spam), to gamble or engage in
Financial loss resulting from legal
other activities that may not be sanctioned by
expenses.
the law.
www.theiia.org Auditing Insider Threat Programs 19