Page 391 - ITGC_Audit Guides
P. 391
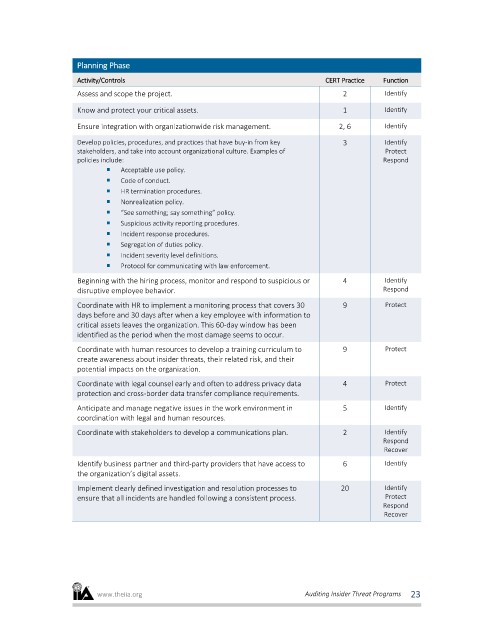
Planning Phase
Activity/Controls CERT Practice Function
Assess and scope the project. 2 Identify
Know and protect your critical assets. 1 Identify
Ensure integration with organizationwide risk management. 2, 6 Identify
Develop policies, procedures, and practices that have buy-in from key 3 Identify
stakeholders, and take into account organizational culture. Examples of Protect
policies include: Respond
Acceptable use policy.
Code of conduct.
HR termination procedures.
Nonrealization policy.
“See something; say something” policy.
Suspicious activity reporting procedures.
Incident response procedures.
Segregation of duties policy.
Incident severity level definitions.
Protocol for communicating with law enforcement.
Beginning with the hiring process, monitor and respond to suspicious or 4 Identify
disruptive employee behavior. Respond
Coordinate with HR to implement a monitoring process that covers 30 9 Protect
days before and 30 days after when a key employee with information to
critical assets leaves the organization. This 60-day window has been
identified as the period when the most damage seems to occur.
Coordinate with human resources to develop a training curriculum to 9 Protect
create awareness about insider threats, their related risk, and their
potential impacts on the organization.
Coordinate with legal counsel early and often to address privacy data 4 Protect
protection and cross-border data transfer compliance requirements.
Anticipate and manage negative issues in the work environment in 5 Identify
coordination with legal and human resources.
Coordinate with stakeholders to develop a communications plan. 2 Identify
Respond
Recover
Identify business partner and third-party providers that have access to 6 Identify
the organization’s digital assets.
Implement clearly defined investigation and resolution processes to 20 Identify
ensure that all incidents are handled following a consistent process. Protect
Respond
Recover
www.theiia.org Auditing Insider Threat Programs 23