Page 392 - ITGC_Audit Guides
P. 392
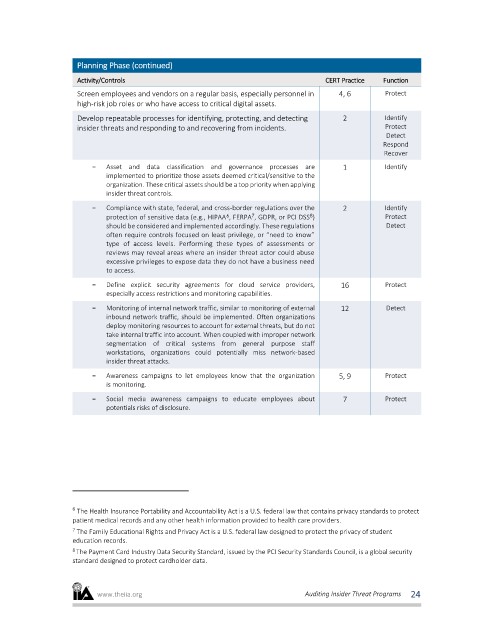
Planning Phase (continued)
Activity/Controls CERT Practice Function
Screen employees and vendors on a regular basis, especially personnel in 4, 6 Protect
high-risk job roles or who have access to critical digital assets.
Develop repeatable processes for identifying, protecting, and detecting 2 Identify
insider threats and responding to and recovering from incidents. Protect
Detect
Respond
Recover
- Asset and data classification and governance processes are 1 Identify
implemented to prioritize those assets deemed critical/sensitive to the
organization. These critical assets should be a top priority when applying
insider threat controls.
- Compliance with state, federal, and cross-border regulations over the 2 Identify
8
7
6
protection of sensitive data (e.g., HIPAA , FERPA , GDPR, or PCI DSS ) Protect
should be considered and implemented accordingly. These regulations Detect
often require controls focused on least privilege, or “need to know”
type of access levels. Performing these types of assessments or
reviews may reveal areas where an insider threat actor could abuse
excessive privileges to expose data they do not have a business need
to access.
- Define explicit security agreements for cloud service providers, 16 Protect
especially access restrictions and monitoring capabilities.
- Monitoring of internal network traffic, similar to monitoring of external 12 Detect
inbound network traffic, should be implemented. Often organizations
deploy monitoring resources to account for external threats, but do not
take internal traffic into account. When coupled with improper network
segmentation of critical systems from general purpose staff
workstations, organizations could potentially miss network-based
insider threat attacks.
- Awareness campaigns to let employees know that the organization 5, 9 Protect
is monitoring.
- Social media awareness campaigns to educate employees about 7 Protect
potentials risks of disclosure.
6 The Health Insurance Portability and Accountability Act is a U.S. federal law that contains privacy standards to protect
patient medical records and any other health information provided to health care providers.
7 The Family Educational Rights and Privacy Act is a U.S. federal law designed to protect the privacy of student
education records.
8 The Payment Card Industry Data Security Standard, issued by the PCI Security Standards Council, is a global security
standard designed to protect cardholder data.
www.theiia.org Auditing Insider Threat Programs 24