Page 390 - ITGC_Audit Guides
P. 390
Preparing the Work Program
The engagement work program is the product of the engagement planning phase. For assurance
engagements, the work program should describe the engagement objectives, scope, risks,
controls, and the procedures that will be used to identify, analyze, evaluate, and document the
information while performing the engagement (Standard 2240 – Engagement Work Program and
Standard 2240.A1). For consulting engagements, work programs may vary in form and content
depending upon the nature of the engagement (Standard 2240.C1).
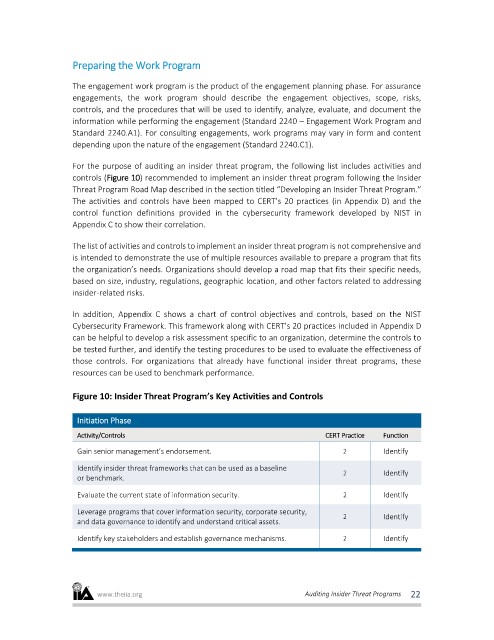
For the purpose of auditing an insider threat program, the following list includes activities and
controls (Figure 10) recommended to implement an insider threat program following the Insider
Threat Program Road Map described in the section titled “Developing an Insider Threat Program.”
The activities and controls have been mapped to CERT’s 20 practices (in Appendix D) and the
control function definitions provided in the cybersecurity framework developed by NIST in
Appendix C to show their correlation.
The list of activities and controls to implement an insider threat program is not comprehensive and
is intended to demonstrate the use of multiple resources available to prepare a program that fits
the organization’s needs. Organizations should develop a road map that fits their specific needs,
based on size, industry, regulations, geographic location, and other factors related to addressing
insider-related risks.
In addition, Appendix C shows a chart of control objectives and controls, based on the NIST
Cybersecurity Framework. This framework along with CERT’s 20 practices included in Appendix D
can be helpful to develop a risk assessment specific to an organization, determine the controls to
be tested further, and identify the testing procedures to be used to evaluate the effectiveness of
those controls. For organizations that already have functional insider threat programs, these
resources can be used to benchmark performance.
Figure 10: Insider Threat Program’s Key Activities and Controls
Initiation Phase
Activity/Controls CERT Practice Function
Gain senior management’s endorsement. 2 Identify
Identify insider threat frameworks that can be used as a baseline
2 Identify
or benchmark.
Evaluate the current state of information security. 2 Identify
Leverage programs that cover information security, corporate security,
2 Identify
and data governance to identify and understand critical assets.
Identify key stakeholders and establish governance mechanisms. 2 Identify
www.theiia.org Auditing Insider Threat Programs 22