Page 395 - ITGC_Audit Guides
P. 395
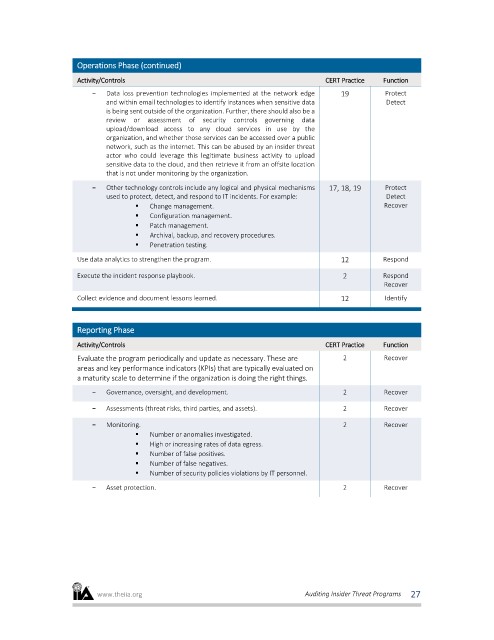
Operations Phase (continued)
Activity/Controls CERT Practice Function
- Data loss prevention technologies implemented at the network edge 19 Protect
and within email technologies to identify instances when sensitive data Detect
is being sent outside of the organization. Further, there should also be a
review or assessment of security controls governing data
upload/download access to any cloud services in use by the
organization, and whether those services can be accessed over a public
network, such as the internet. This can be abused by an insider threat
actor who could leverage this legitimate business activity to upload
sensitive data to the cloud, and then retrieve it from an offsite location
that is not under monitoring by the organization.
- Other technology controls include any logical and physical mechanisms 17, 18, 19 Protect
used to protect, detect, and respond to IT incidents. For example: Detect
Change management. Recover
Configuration management.
Patch management.
Archival, backup, and recovery procedures.
Penetration testing.
Use data analytics to strengthen the program. 12 Respond
Execute the incident response playbook. 2 Respond
Recover
Collect evidence and document lessons learned. 12 Identify
Reporting Phase
Activity/Controls CERT Practice Function
Evaluate the program periodically and update as necessary. These are 2 Recover
areas and key performance indicators (KPIs) that are typically evaluated on
a maturity scale to determine if the organization is doing the right things.
- Governance, oversight, and development. 2 Recover
- Assessments (threat risks, third parties, and assets). 2 Recover
- Monitoring. 2 Recover
Number or anomalies investigated.
High or increasing rates of data egress.
Number of false positives.
Number of false negatives.
Number of security policies violations by IT personnel.
- Asset protection. 2 Recover
www.theiia.org Auditing Insider Threat Programs 27