Page 412 - Handbook of Modern Telecommunications
P. 412
Network Management and Administration 3-203
Monitoring billions
Network of events for thousands
wide
of targets
Intercept and summarizing
information by correlation
and association
Target
specific Intelligence
Re-target
Intercept to complete
information demand
Content
specific
Intelligence
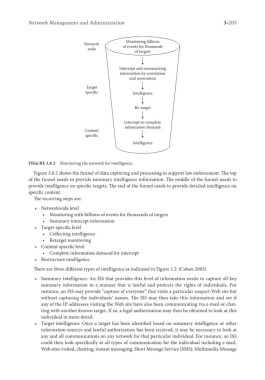
FIGu RE 3.8.2 Monitoring the network for intelligence.
Figure 3.8.2 shows the funnel of data capturing and processing to support law enforcement. The top
of the funnel needs to provide summary intelligence information. The middle of the funnel needs to
provide intelligence on specific targets. The end of the funnel needs to provide detailed intelligence on
specific content.
The recurring steps are:
• Networkwide level
• Monitoring with billions of events for thousands of targets
• Summary intercept information
• Target-specific level
• Collecting intelligence
• Retarget monitoring
• Content-specific level
• Complete information demand for intercept
• Restructure intelligence
There are three different types of intelligence as indicated in Figure 1.2: (Cohen 2003).
• Summary intelligence: An ISS that provides this level of information needs to capture all key
summary information in a manner that is lawful and protects the rights of individuals. For
instance, an ISS may provide “capture of everyone” that visits a particular suspect Web site but
without capturing the individuals’ names. The ISS may then take this information and see if
any of the IP addresses visiting the Web site have also been communicating via e-mail or chat-
ting with another known target. If so, a legal authorization may then be obtained to look at this
individual in more detail.
• Target intelligence: Once a target has been identified based on summary intelligence or other
information sources and lawful authorization has been received, it may be necessary to look at
any and all communications on any network for that particular individual. For instance, an ISS
could then look specifically at all types of communication for the individual including e-mail,
Web sites visited, chatting, instant messaging, Short Message Service (SMS), Multimedia Message