Page 13 - 2023-Mar-Apr-Journal
P. 13
The “Angle of Repose”
Business Interruption and Continuity Losses from Cyberattacks
John Southrey, Cyberinsurance/Cybersecurity Consultant
I lost and how quickly operations can be making it inaccessible. Phishing/social
have been smitten with the Grand
restored. Practices who cannot restore
Canyon of Arizona since 1979 and
engineering/business email compromise
have backpacked into this park
do not maintain contemporaneous or
malicious websites designed to exploit
nearly forty times. During one of my their data in a timely manner and who scams—using phony emails and
remote off-trail hikes, I recall navigating real-time data backups will typically human nature—are key attack vectors,
down a steep ravine to a perilous scree have a more extensive business and unsuspecting employees are
slope and then scrambling down it interruption loss. considered the weakest cybersecurity
carefully because it seemed above the The financial impact of a data link. Unfortunately, many cyber breaches
angle of repose . breach creates both direct and indirect occur due to human error.
1
What does my Grand Canyon costs. The direct costs can include Today’s virtual work environment
experience have to do with health care, expenses for legal fees; patient and and its reliance on mobile devices
you ask? As a professional commercial media notifications; forensics and data connected to company networks, as well
and cyber insurance consultant for many restoration; public relations; credit as widespread reliance on third-party
years, my story is analogous to the monitoring services; call center support; vendors for data processing tasks, has
health care provider’s angle of repose and regulatory fines and penalties. The increased the ingress and egress for a
with respect to navigating business indirect costs can include the loss of business interruption loss. For example:
interruption and business continuity/ income; loss of patient goodwill and • A malicious hacker exploits
reputational losses from malicious business reputation; and additional weaknesses in a medical practices’
cyberattacks. A simple cybersecurity expenses to mitigate the interruption computer system and disables all access
misstep can result in a precipitous in operations. to the physician’s ePHI and accounting
interruption, as restoring damaged or At some point, the financial angle systems, resulting in downtime and a loss
lost data can impair business operations of repose from a business interruption of revenue.
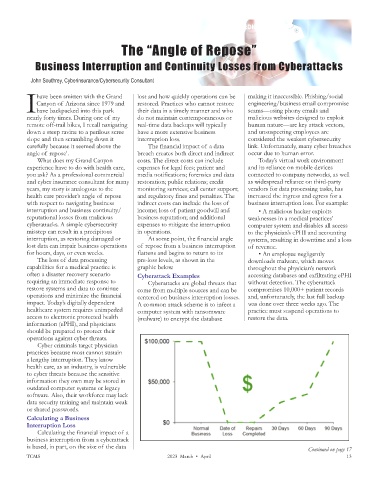
for hours, days, or even weeks. flattens and begins to return to its • An employee negligently
The loss of data processing pre-loss levels, as shown in the downloads malware, which moves
capabilities for a medical practice is graphic below. throughout the physician’s network
often a disaster recovery scenario Cyberattack Examples accessing databases and exfiltrating ePHI
requiring an immediate response to Cyberattacks are global threats that without detection. The cyberattack
restore systems and data to continue come from multiple sources and can be compromises 10,000+ patient records
operations and minimize the financial centered on business interruption losses. and, unfortunately, the last full backup
impact. Today’s digitally dependent A common attack scheme is to infect a was done over three weeks ago. The
healthcare system requires unimpeded computer system with ransomware practice must suspend operations to
access to electronic protected health (malware) to encrypt the database restore the data.
information (ePHI), and physicians
should be prepared to protect their
operations against cyber threats.
Cyber criminals target physician
practices because most cannot sustain
a lengthy interruption. They know
health care, as an industry, is vulnerable
to cyber threats because the sensitive
information they own may be stored in
outdated computer systems or legacy
software. Also, their workforce may lack
data security training and maintain weak
or shared passwords.
Calculating a Business
Interruption Loss
Calculating the financial impact of a
business interruption from a cyberattack
is based, in part, on the size of the data Continued on page 17
TCMS 2023 March • April 13