Page 453 - StudyBook.pdf
P. 453
Topologies and IDS • Chapter 7 437
This multi-segment approach allows flexibility, because new segments with spe-
cific purposes and security requirements can be easily added to the model. In gen-
eral, the two segments that are widely accepted are:
■ A segment dedicated to information storage
■ A segment specifically for the processing of business information
Each of these two new segments has special security and operability concerns
above and beyond those of the rest of the organizational Intranet. In reality, every-
thing comes down to dollars—what is it going to cost to implement a security
solution versus what will it cost if the system is breached by attackers.Thus the
value of raw data is different than the value of the financial processing system. Each
possible solution has its pluses and minuses, but in the end a balance is struck
between cost versus expected results.Thus, the creation of different zones (seg-
ments) for different purposes. Note that the Web and e-mail servers would likely
receive the least amount of spending and security measures, which is not to say that
they will be completely ignored, they just would not receive as much as the finan-
cial servers might.
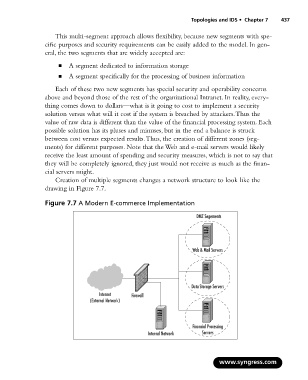
Creation of multiple segments changes a network structure to look like the
drawing in Figure 7.7.
Figure 7.7 A Modern E-commerce Implementation
DMZ Segements
Web & Mail Servers
Data Storage Servers
Internet Firewall
(External Network)
Financial Processing
Internal Network Servers
www.syngress.com