Page 450 - StudyBook.pdf
P. 450
434 Chapter 7 • Topologies and IDS
trusted by the systems in the protected network.A good first step in building a
strong defense is to harden the DMZ systems by removing all unnecessary services
and unneeded components.The result is a bastion host.This scenario allows for
public services while still maintaining a degree of protection against attack.
EXAM WARNING
Hosts located in a DMZ are generally accessed from both internal net-
work clients and public (external) Internet clients. Examples of DMZ bas-
tion hosts are DNS servers, Web servers, and File Transfer Protocol (FTP)
servers. A bastion host is a system on the public side of the firewall,
which is exposed to attack. The word bastion comes from sixteenth cen-
tury French word, meaning the projecting part of a fortress wall that
faces the outside and is exposed to attackers.
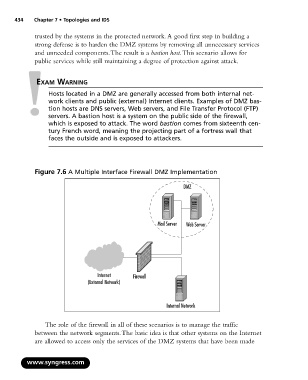
Figure 7.6 A Multiple Interface Firewall DMZ Implementation
DMZ
Mail Server Web Server
Internet Firewall
(External Network)
Internal Network
The role of the firewall in all of these scenarios is to manage the traffic
between the network segments.The basic idea is that other systems on the Internet
are allowed to access only the services of the DMZ systems that have been made
www.syngress.com