Page 446 - StudyBook.pdf
P. 446
430 Chapter 7 • Topologies and IDS
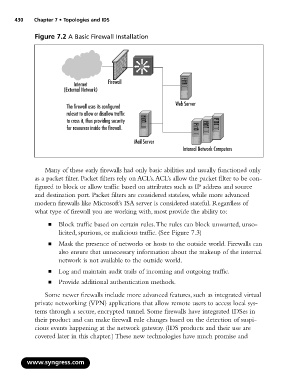
Figure 7.2 A Basic Firewall Installation
Internet Firewall
(External Network)
Web Server
The firewall uses its configured
ruleset to allow or disallow traffic
to cross it, thus providing security
for resources inside the firewall.
Mail Server
Internal Network Computers
Many of these early firewalls had only basic abilities and usually functioned only
as a packet filter. Packet filters rely on ACL’s.ACL’s allow the packet filter to be con-
figured to block or allow traffic based on attributes such as IP address and source
and destination port. Packet filters are considered stateless, while more advanced
modern firewalls like Microsoft’s ISA server is considered stateful. Regardless of
what type of firewall you are working with, most provide the ability to:
■ Block traffic based on certain rules.The rules can block unwanted, unso-
licited, spurious, or malicious traffic. (See Figure 7.3)
■ Mask the presence of networks or hosts to the outside world. Firewalls can
also ensure that unnecessary information about the makeup of the internal
network is not available to the outside world.
■ Log and maintain audit trails of incoming and outgoing traffic.
■ Provide additional authentication methods.
Some newer firewalls include more advanced features, such as integrated virtual
private networking (VPN) applications that allow remote users to access local sys-
tems through a secure, encrypted tunnel. Some firewalls have integrated IDSes in
their product and can make firewall rule changes based on the detection of suspi-
cious events happening at the network gateway. (IDS products and their use are
covered later in this chapter.) These new technologies have much promise and
www.syngress.com