Page 578 - StudyBook.pdf
P. 578
562 Chapter 10 • Public Key Infrastructure
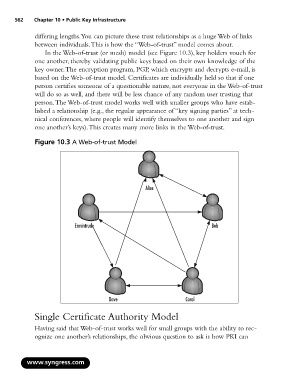
differing lengths.You can picture these trust relationships as a huge Web of links
between individuals.This is how the “Web-of-trust” model comes about.
In the Web-of-trust (or mesh) model (see Figure 10.3), key holders vouch for
one another, thereby validating public keys based on their own knowledge of the
key owner.The encryption program, PGP, which encrypts and decrypts e-mail, is
based on the Web-of-trust model. Certificates are individually held so that if one
person certifies someone of a questionable nature, not everyone in the Web-of-trust
will do so as well, and there will be less chance of any random user trusting that
person.The Web-of-trust model works well with smaller groups who have estab-
lished a relationship (e.g., the regular appearance of “key signing parties” at tech-
nical conferences, where people will identify themselves to one another and sign
one another’s keys).This creates many more links in the Web-of-trust.
Figure 10.3 A Web-of-trust Model
Alice
Ermintrude Bob
Dave Carol
Single Certificate Authority Model
Having said that Web-of-trust works well for small groups with the ability to rec-
ognize one another’s relationships, the obvious question to ask is how PKI can
www.syngress.com