Page 581 - StudyBook.pdf
P. 581
Public Key Infrastructure • Chapter 10 565
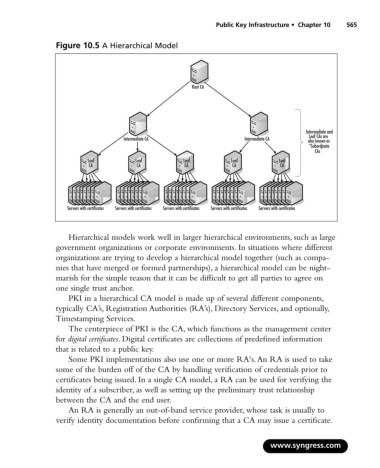
Figure 10.5 A Hierarchical Model
Root CA
Intermediate and
Leaf CAs are
Intermediate CA Intermediate CA also known as
“Subordinate
CAs "
Leaf Leaf Leaf Leaf Leaf
CA CA CA CA CA
Servers with certificates Servers with certificates Servers with certificates Servers with certificates Servers with certificates
Hierarchical models work well in larger hierarchical environments, such as large
government organizations or corporate environments. In situations where different
organizations are trying to develop a hierarchical model together (such as compa-
nies that have merged or formed partnerships), a hierarchical model can be night-
marish for the simple reason that it can be difficult to get all parties to agree on
one single trust anchor.
PKI in a hierarchical CA model is made up of several different components,
typically CA’s, Registration Authorities (RA’s), Directory Services, and optionally,
Timestamping Services.
The centerpiece of PKI is the CA, which functions as the management center
for digital certificates. Digital certificates are collections of predefined information
that is related to a public key.
Some PKI implementations also use one or more RA‘s.An RA is used to take
some of the burden off of the CA by handling verification of credentials prior to
certificates being issued. In a single CA model, a RA can be used for verifying the
identity of a subscriber, as well as setting up the preliminary trust relationship
between the CA and the end user.
An RA is generally an out-of-band service provider, whose task is usually to
verify identity documentation before confirming that a CA may issue a certificate.
www.syngress.com