Page 583 - StudyBook.pdf
P. 583
Public Key Infrastructure • Chapter 10 567
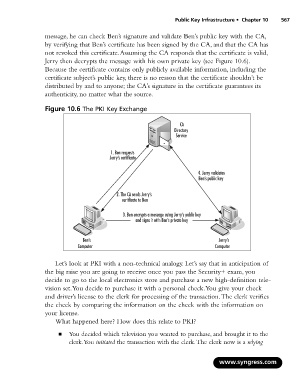
message, he can check Ben’s signature and validate Ben’s public key with the CA,
by verifying that Ben’s certificate has been signed by the CA, and that the CA has
not revoked this certificate.Assuming the CA responds that the certificate is valid,
Jerry then decrypts the message with his own private key (see Figure 10.6).
Because the certificate contains only publicly available information, including the
certificate subject’s public key, there is no reason that the certificate shouldn’t be
distributed by and to anyone; the CA’s signature in the certificate guarantees its
authenticity, no matter what the source.
Figure 10.6 The PKI Key Exchange
CA
Directory
Service
1. Ben requests
Jerry’s certificate
4. Jerry validates
Ben’s public key
2. The CA sends Jerry’s
certificate to Ben
3. Ben encrypts a message using Jerry’s public key
and signs it with Ben’s private key .
Ben’s Jerry’s
Computer Computer
Let’s look at PKI with a non-technical analogy. Let’s say that in anticipation of
the big raise you are going to receive once you pass the Security+ exam, you
decide to go to the local electronics store and purchase a new high-definition tele-
vision set.You decide to purchase it with a personal check.You give your check
and driver’s license to the clerk for processing of the transaction.The clerk verifies
the check by comparing the information on the check with the information on
your license.
What happened here? How does this relate to PKI?
■ You decided which television you wanted to purchase, and brought it to the
clerk.You initiated the transaction with the clerk.The clerk now is a relying
www.syngress.com