Page 61 - ISCI’2017
P. 61
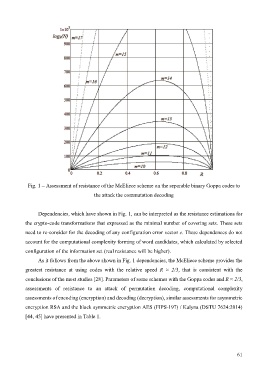
Fig. 1 – Assessment of resistance of the McEliece scheme on the separable binary Goppa codes to
the attack the commutation decoding
Dependencies, which have shown in Fig. 1, can be interpreted as the resistance estimations for
the crypto-code transformations that expressed as the minimal number of covering sets. These sets
need to re-consider for the decoding of any configuration error vector e. These dependences do not
account for the computational complexity forming of word candidates, which calculated by selected
configuration of the information set (real resistance will be higher).
As it follows from the above shown in Fig. 1 dependencies, the McEliece scheme provides the
greatest resistance at using codes with the relative speed R ≈ 2/3, that is consistent with the
conclusions of the most studies [28]. Parameters of some schemes with the Goppa codes and R ≈ 2/3,
assessments of resistance to an attack of permutation decoding, computational complexity
assessments of encoding (encryption) and decoding (decryption), similar assessments for asymmetric
encryption RSA and the block symmetric encryption AES (FIPS-197) / Kalyna (DSTU 7624:2014)
[44, 45] have presented in Table 1.
61