Page 57 - ISCI’2017
P. 57
g r 0 ... 0
g g ... 0
r 1 − r
... ... ... ...
g 1 g 2 ... g r
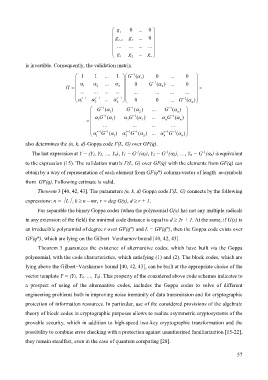
is invertible. Consequently, the validation matrix
( )
−
1
1 1 ... 1 G α 1 0 ... 0
α α ... α 0 G − 1 (α ) ... 0
H = 1 2 n 2 =
... ... ... ... ... ... ... ...
r− 1 r− 1 r− 1
α 1 α 2 ... α n 0 0 ... G − 1 (α n )
G α − 1 ( ) G − 1 (α ) ... G − 1 (α )
1
α G α − 1 ( ) α G − 1 (α 2 ) ... α G − 1 (α n )
= 1 1 2 2 n n
... ... ... ...
r− 1 − 1 r− 1 − 1 r− 1 − 1
α 1 G (α 1 ) α 2 G (α 2 ) ... α n G (α n )
also determines the (n, k, d)-Goppa code Г(L, G) over GF(q).
-1
-1
-1
The last expression at Y = (Y1, Y2, …, Yn), Y1 = G (α1), Y2 = G (α2), …, Yn = G (αn) is equivalent
to the expression (15). The validation matrix Г(L, G) over GF(q) with the elements from GF(q) can
m
obtain by a way of representation of each element from GF(q ) column-vector of length m-symbols
from GF(q). Following estimate is valid.
Theorem 3 [40, 42, 43]. The parameters (n, k, d) Goppa code Г(L, G) connects by the following
expressions: n = L, k ≥ n – mr, r = deg G(x), d ≥ r + 1.
For separable the binary Goppa codes (when the polynomial G(x) has not any multiple radicals
in any extension of the field) the minimal code distance is equal to d ≥ 2r + 1. At the same, if G(x) is
m
an irreducible polynomial of degree r over GF(q ) and L = GF(q ), then the Goppa code exists over
m
m
GF(q ), which are lying on the Gilbert–Varshamov bound [40, 42, 43].
Theorem 3 guarantees the existence of alternantive codes, which have built via the Goppa
polynomial, with the code characteristics, which satisfying (1) and (2). The block codes, which are
lying above the Gilbert–Varshamov bound [40, 42, 43], can be built at the appropriate choice of the
vector template Y = (Y1, Y2, …, Yn). This property of the considered above code schemes indicates to
a prospect of using of the alternantive codes, includes the Goppa codes to solve of different
engineering problems both in improving noise immunity of data transmission and for cryptographic
protection of information resources. In particular, use of the considered provisions of the algebraic
theory of block codes in cryptographic purposes allows to realize asymmetric cryptosystems of the
provable security, which in addition to high-speed two-key cryptographic transformation and the
possibility to combine error checking with a protection against unauthorized familiarization [15-22],
they remain steadfast, even in the case of quantum computing [28].
57