Page 61 - NCS Sales Manual 2018.pdf
P. 61
CYBER SECURITY
MANAGED SECURITY SERVICES
As a global managed security services provider (MSSP), we know security cannot be an afterthought. That is why our comprehensive services are designed to take care of
cyber threats and risks that arise in this new converged IT and OT landscape, so you are enabled to run your world.
We help secure global enterprises operating in 96 countries with our award-winning cyber security services:
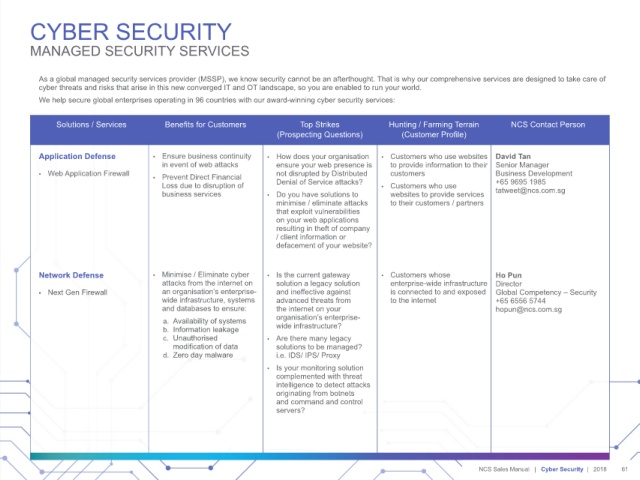
Solutions / Services Benefits for Customers Top Strikes Hunting / Farming Terrain NCS Contact Person
(Prospecting Questions) (Customer Profile)
Application Defense • Ensure business continuity • How does your organisation • Customers who use websites David Tan
in event of web attacks ensure your web presence is to provide information to their Senior Manager
• Web Application Firewall • Prevent Direct Financial not disrupted by Distributed customers Business Development
Loss due to disruption of Denial of Service attacks? • Customers who use +65 9695 1985
tatweet@ncs.com.sg
business services • Do you have solutions to websites to provide services
minimise / eliminate attacks to their customers / partners
that exploit vulnerabilities
on your web applications
resulting in theft of company
/ client information or
defacement of your website?
Network Defense • Minimise / Eliminate cyber • Is the current gateway • Customers whose Ho Pun
attacks from the internet on solution a legacy solution enterprise-wide infrastructure Director
• Next Gen Firewall an organisation’s enterprise- and ineffective against is connected to and exposed Global Competency – Security
wide infrastructure, systems advanced threats from to the internet +65 6556 5744
and databases to ensure: the internet on your hopun@ncs.com.sg
a. Availability of systems organisation’s enterprise-
b. Information leakage wide infrastructure?
c. Unauthorised • Are there many legacy
modification of data solutions to be managed?
d. Zero day malware i.e. IDS/ IPS/ Proxy
• Is your monitoring solution
complemented with threat
intelligence to detect attacks
originating from botnets
and command and control
servers?
NCS Sales Manual | Cyber Security | 2018 61