Page 62 - NCS Sales Manual 2018.pdf
P. 62
CYBER SECURITY
MANAGED SECURITY SERVICES
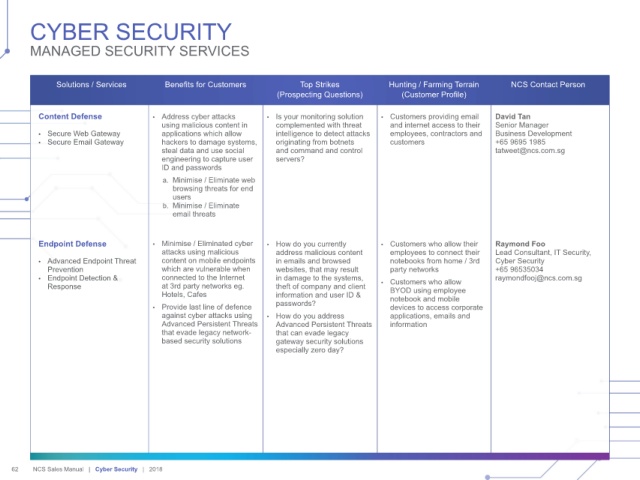
Solutions / Services Benefits for Customers Top Strikes Hunting / Farming Terrain NCS Contact Person
(Prospecting Questions) (Customer Profile)
Content Defense • Address cyber attacks • Is your monitoring solution • Customers providing email David Tan
using malicious content in complemented with threat and internet access to their Senior Manager
• Secure Web Gateway applications which allow intelligence to detect attacks employees, contractors and Business Development
• Secure Email Gateway hackers to damage systems, originating from botnets customers +65 9695 1985
steal data and use social and command and control tatweet@ncs.com.sg
engineering to capture user servers?
ID and passwords
a. Minimise / Eliminate web
browsing threats for end
users
b. Minimise / Eliminate
email threats
Endpoint Defense • Minimise / Eliminated cyber • How do you currently • Customers who allow their Raymond Foo
attacks using malicious address malicious content employees to connect their Lead Consultant, IT Security,
• Advanced Endpoint Threat content on mobile endpoints in emails and browsed notebooks from home / 3rd Cyber Security
Prevention which are vulnerable when websites, that may result party networks +65 96535034
• Endpoint Detection & connected to the Internet in damage to the systems, • Customers who allow raymondfooj@ncs.com.sg
Response at 3rd party networks eg. theft of company and client BYOD using employee
Hotels, Cafes information and user ID & notebook and mobile
• Provide last line of defence passwords? devices to access corporate
against cyber attacks using • How do you address applications, emails and
Advanced Persistent Threats Advanced Persistent Threats information
that evade legacy network- that can evade legacy
based security solutions gateway security solutions
especially zero day?
62 NCS Sales Manual | Cyber Security | 2018