Page 63 - NCS Sales Manual 2018.pdf
P. 63
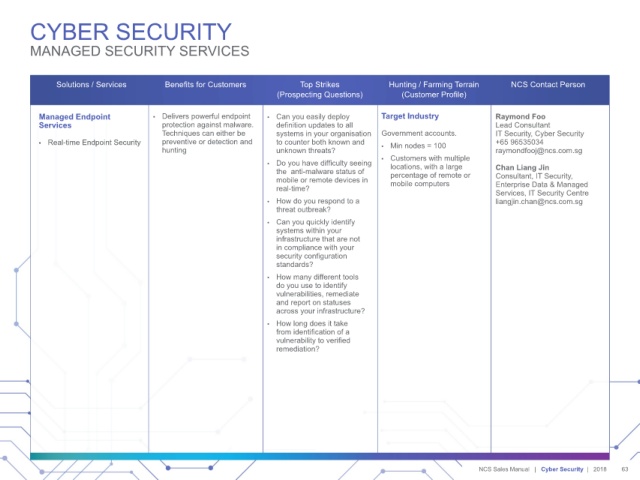
CYBER SECURITY
MANAGED SECURITY SERVICES
Solutions / Services Benefits for Customers Top Strikes Hunting / Farming Terrain NCS Contact Person
(Prospecting Questions) (Customer Profile)
Managed Endpoint • Delivers powerful endpoint • Can you easily deploy Target Industry Raymond Foo
Services protection against malware. definition updates to all Lead Consultant
Techniques can either be systems in your organisation Government accounts. IT Security, Cyber Security
• Real-time Endpoint Security preventive or detection and to counter both known and • Min nodes = 100 +65 96535034
hunting unknown threats? raymondfooj@ncs.com.sg
• Do you have difficulty seeing • Customers with multiple Chan Liang Jin
locations, with a large
the anti-malware status of percentage of remote or
mobile or remote devices in mobile computers Consultant, IT Security,
Enterprise Data & Managed
real-time? Services, IT Security Centre
• How do you respond to a liangjin.chan@ncs.com.sg
threat outbreak?
• Can you quickly identify
systems within your
infrastructure that are not
in compliance with your
security configuration
standards?
• How many different tools
do you use to identify
vulnerabilities, remediate
and report on statuses
across your infrastructure?
• How long does it take
from identification of a
vulnerability to verified
remediation?
NCS Sales Manual | Cyber Security | 2018 63