Page 73 - Internal Auditing Standards
P. 73
Guide to Using International Standards on Auditing in the Audits of Small- and Medium-Sized Entities Volume 1—Core Concepts
• Communications relating to internal control from external auditors and consultants.
Sources of Information Used for Monitoring
Much of the information used in monitoring will be produced by the entity’s information system.
Management may tend to assume that this information is accurate. If this information is not accurate, there is
a risk that management could reach incorrect conclusions, and make poor decisions as a result.
Accordingly, when the auditor is evaluating the monitoring of controls, an understanding is required of:
• The sources of the information related to the entity’s monitoring activities; and
• The basis upon which management considers the information to be sufficiently reliable for the purpose.
5.9 Understanding of Internal Controls Relevant to the Audit
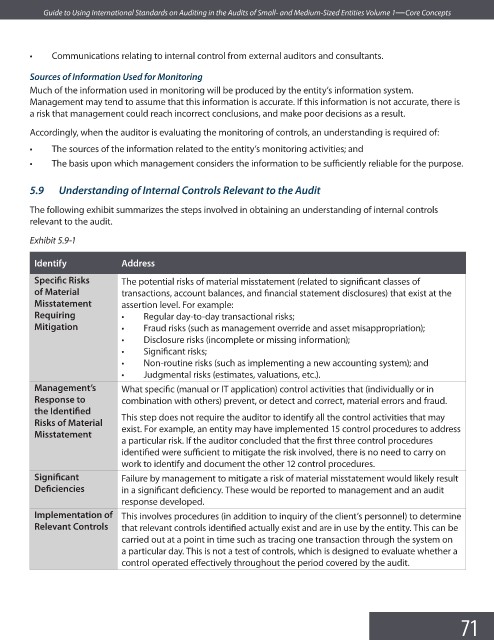
The following exhibit summarizes the steps involved in obtaining an understanding of internal controls
relevant to the audit.
Exhibit 5.9-1
Identify Address
Specifi c Risks The potential risks of material misstatement (related to significant classes of
of Material transactions, account balances, and financial statement disclosures) that exist at the
Misstatement assertion level. For example:
Requiring • Regular day-to-day transactional risks;
Mitigation • Fraud risks (such as management override and asset misappropriation);
• Disclosure risks (incomplete or missing information);
• Signifi cant risks;
• Non-routine risks (such as implementing a new accounting system); and
• Judgmental risks (estimates, valuations, etc.).
Management’s What specific (manual or IT application) control activities that (individually or in
Response to combination with others) prevent, or detect and correct, material errors and fraud.
the Identifi ed
This step does not require the auditor to identify all the control activities that may
Risks of Material
exist. For example, an entity may have implemented 15 control procedures to address
Misstatement
a particular risk. If the auditor concluded that the first three control procedures
identified were sufficient to mitigate the risk involved, there is no need to carry on
work to identify and document the other 12 control procedures.
Signifi cant Failure by management to mitigate a risk of material misstatement would likely result
Defi ciencies in a signifi cant deficiency. These would be reported to management and an audit
response developed.
Implementation of This involves procedures (in addition to inquiry of the client’s personnel) to determine
Relevant Controls that relevant controls identified actually exist and are in use by the entity. This can be
carried out at a point in time such as tracing one transaction through the system on
a particular day. This is not a test of controls, which is designed to evaluate whether a
control operated effectively throughout the period covered by the audit.
71