Page 14 - ONLINE SERVICE
P. 14
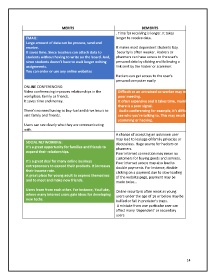
MERITS DEMERITS
. Time for receiving is longer. It takes
EMAIL: longer to receive data.
Large amount of data can be process, send and
receive. It makes most dependent students lazy.
It saves time. Since teachers can attach data to Security is often weaker. Hackers or
students without having to write on the board. And, pharmers can have access to the user’s
since students doesn’t have to wait longer writing personal data by clicking and following a
assignments. link sent by the hacker or scammer.
You can enter or use any online websites
Hackers can get access to the user’s
. personal computer easily
ONLINE CONFERENCING:
Video conferencing improves relationships in the Difficult or an untrained co-worker may mean
workplace, family or friends. poor meeting.
It saves time and money. It often expensive and it takes time, mainly where
there is a poor signal.
There’s no need having to buy fuel and drive hours to Audio conferencing for example, it’s difficult to
visit family and friends. see who you’re talking to. This may result in
scamming or hacking.
Users can see clearly who they are communicating
with.
A chance of accepting an unknown user
may lead to leakage of family privacies or
SOCIAL NETWORKING: discussions. Huge source for hackers or
It’s a great opportunity for families and friends to pharmers.
expend their relationships. Poor internet connection may mean no
customers for buying goods and services.
It’s a great deal for many online business Poor internet access may also lead to
entrepreneurs to expend their products. It increases double payments. For instance, double
their income rate. clicking on a payment due to slow loading
A great place for young adult to express themselves of the website page, payment may be
and to meet and make new friends. made twice…
Users learn from each other. For instance, YouTube, Online security is often weak as young
where many internet users gain ideas for developing
users under the age of 16 or below may be
new techs.
bullied or fall in predator’s traps.
A mistake from one particular user can
affect many ‘dependent’ or secondary
users.
14