Page 21 - 10. Gi_Dec-Jan2019_LR
P. 21
maintenance of a safety-instrumented
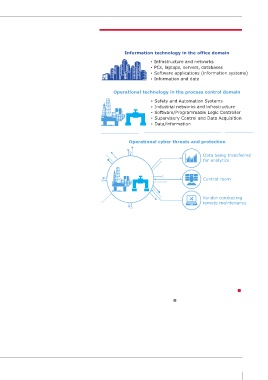
system. DNVGL-RP-G108 applies not FIGURE 1 Managing cyber risk across IT and OT
only to new installations; existing and
more mature assets may need to be
updated to prevent and protect n ormation technolo in the o ice domain
against cyber threats.
The RP is intended to include all
elements – people, processes,
technology – to ensure cyber security is
addressed in industrial automation and
control systems. This includes the asset
owner/operator, system integrator,
product supplier, service provider and perational technolo in the process control domain
compliance authority. The practice
explains shared responsibilities and
describes who performs activities, who
should be involved, and the expected L
inputs and outputs. D
D
SIMULATING ATTACKS TO
IDENTIFY CYBER
VULNERABILITY
Simulating a cyber-attack on a pipeline perational c er threats and protection
system can demonstrate strengths
and weaknesses within an organisation
and is a practical exercise to start D
building defences. Some companies,
including DNV GL, recruit and develop
‘ethical hackers’ to perform testing
and verication of OT, IT and linkages
between them. 2
DNV GL’s ethical hackers combine
hacking expertise with profound
domain knowledge of OT. V
The ethical hacking process begins
with passive and active reconnaissance
of an asset or system’s cyber security.
Remote metering of infrastructure ©2017 DNV GL
scans for potential vulnerabilities, for
example. If any are found, the next
step is to try to gain access through critical, cyber-enabled infrastructure, technical capabilities and related
penetration testing to reveal actual such as gas networks. Applied at the processes, and of technical and
vulnerabilities and help customers concept phase, it can then be used to organisational measures.
mitigate risk. validate the eectiveness of the The technical implementation and
From the use of default system barriers that were initially designed conguration in the industrial
passwords and missing patching, to into the integrated system. automation and control system, and
unsecured WiFi providing a route into DNV GL’s Technical Assurance how this system is operated,
control systems, vulnerabilities can be Laboratory oers tools and techniques maintained, and deployed will be
simple. Ethical hackers also scan for to detect device aws as part of a reected in the protection level. DNV
weaknesses in customer OT and IT product security evaluation service GL intends to update DNVGL-
systems that could be used to enter currently being applied in the sector. RP-G108 regularly to incorporate
and exploit the system to aect This service includes applying ethical industry experience, new and updated
operations or access condential hacking techniques to products. standards, and fresh developments. ■
information. Some of this scanning and
testing can be carried out remotely. KEEPING UP WITH STANDARDS ■ Download DNV GL’s Recommended
Cyber security is an ever-changing Practice at www.dnvgl.com/oilgas/
ETHICAL HACKING FOR challenge, requiring continual download/dnvgl-rp-g108-cyber-
VERIFICATION AND updates to standards. IEC 62443 security-in-the-oil-and-gas-industry-
TECHNICAL QUALIFICATION committees will likely issue a new based-on-IEC-62443.html
Ethical hacking can also assist the standard for protection levels in the
verication and technical qualication future, for instance. Protection level REFERENCES
of equipment and systems. is a methodology for evaluating 1. Condence and control: The outlook for the oil and gas
Penetration testing is a relevant protection of plants in operation. It industry in 2018, DNV GL, January 2018
2. Ethical hacking: The white hats in DNV GL cyber security
third-party verication step for any includes combined evaluation of services, K Ording, DNV GL
21
CyberSecurityFromDNV_V2.indd 2 15/11/2018 14:29