Page 181 - Deception at work all chapters EBook
P. 181
182 Deception at Work
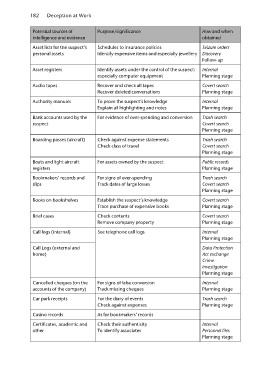
Potential sources of Purpose/significance How and when
intelligence and evidence obtained
Asset lists for the suspect’s
personal assets Schedules to insurance policies Seizure orders
Asset registers Identify expensive items and especially jewellery Discovery
Audio tapes Follow-up
Authority manuals Identify assets under the control of the suspect: Internal
Bank accounts used by the especially computer equipment Planning stage
suspect
Recover and check all tapes Covert search
Boarding passes (aircraft) Recover deleted conversations Planning stage
Boats and light aircraft To prove the suspect’s knowledge Internal
registers Explain all highlighting and notes Planning stage
Bookmakers’ records and
slips For evidence of over-spending and conversion Trash search
Covert search
Books on bookshelves Planning stage
Brief cases Check against expense statements Trash search
Check class of travel Covert search
Call logs (internal) Planning stage
Call Logs (external and For assets owned by the suspect Public records
home) Planning stage
Cancelled cheques (on the For signs of over-spending Trash search
accounts of the company) Track dates of large losses Covert search
Car park receipts Planning stage
Casino records Establish the suspect’s knowledge Covert search
Certificates, academic and Trace purchase of expensive books Planning stage
other
Check contents Covert search
Remove company property Planning stage
See telephone call logs Internal
Planning stage
Data Protection
Act exchange
Crime
investigation
Planning stage
For signs of false conversion Internal
Track missing cheques Planning stage
For the diary of events Trash search
Check against expenses Planning stage
As for bookmakers’ records
Check their authenticity Internal
To identify associates Personnel files
Planning stage