Page 185 - Deception at work all chapters EBook
P. 185
186 Deception at Work
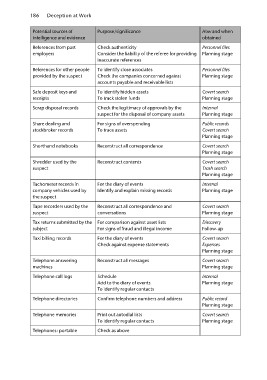
Potential sources of Purpose/significance How and when
intelligence and evidence obtained
References from past Check authenticity Personnel files
employers
Consider the liability of the referee for providing Planning stage
inaccurate references
References for other people To identify close associates Personnel files
provided by the suspect Check the companies concerned against Planning stage
accounts payable and receivable lists
Safe deposit keys and To identify hidden assets Covert search
receipts To track stolen funds Planning stage
Scrap disposal records Check the legitimacy of approvals by the Internal
suspect for the disposal of company assets Planning stage
Share dealing and For signs of overspending Public records
stockbroker records To trace assets Covert search
Planning stage
Shorthand notebooks Reconstruct all correspondence Covert search
Planning stage
Shredder used by the Reconstruct contents Covert search
suspect Trash search
Planning stage
Tachometer records in For the diary of events Internal
company vehicles used by Identify and explain missing records Planning stage
the suspect
Tape recorders used by the Reconstruct all correspondence and Covert search
suspect conversations Planning stage
Tax returns submitted by the For comparison against asset lists Discovery
Follow-up
subject For signs of fraud and illegal income
Taxi billing records For the diary of events Covert search
Check against expense statements Expenses
Planning stage
Telephone answering Reconstruct all messages Covert search
machines Planning stage
Telephone call logs Schedule Internal
Add to the diary of events Planning stage
To identify regular contacts
Telephone directories Confirm telephone numbers and address Public record
Planning stage
Telephone memories Print out autodial lists Covert search
To identify regular contacts Planning stage
Telephones: portable Check as above