Page 183 - Deception at work all chapters EBook
P. 183
184 Deception at Work
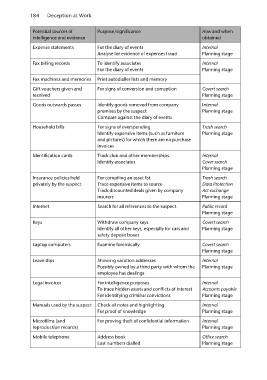
Potential sources of Purpose/significance How and when
intelligence and evidence obtained
Internal
Expense statements For the diary of events Planning stage
Analyse for evidence of expenses fraud Internal
Planning stage
Fax billing records To identify associates
For the diary of events Covert search
Planning stage
Fax machines and memories Print autodialler lists and memory Internal
Planning stage
Gift vouchers given and For signs of conversion and corruption
received Trash search
Planning stage
Goods outwards passes Identify goods removed from company
premises by the suspect Internal
Compare against the diary of events Cover search
Planning stage
Household bills For signs of overspending Trash search
Identify expensive items (such as furniture Data Protection
and pictures) for which there are no purchase Act exchange
invoices Planning stage
Public record
Identification cards Track club and other memberships Planning stage
Identify associates Covert search
Planning stage
Insurance policies held For compiling an asset list
privately by the suspect Trace expensive items to source Covert search
Track discounted deals given by company Planning stage
Internet insurers Internal
Planning stage
Search for all references to the suspect
Internal
Keys Withdraw company keys Accounts payable
Laptop computers Identify all other keys, especially for cars and Planning stage
safety deposit boxes Internal
Planning stage
Examine forensically Internal
Planning stage
Leave slips Showing vacation addresses Office search
Possibly owned by a third party with whom the Planning stage
employee has dealings
Legal invoices For intelligence purposes
To trace hidden assets and conflicts of interest
For identifying criminal convictions
Manuals used by the suspect Check all notes and highlighting
For proof of knowledge
Microfilms (and For proving theft of confidential information
reproduction records)
Mobile telephone Address book
Last numbers dialled