Page 182 - Deception at work all chapters EBook
P. 182
Planning Investigations and Legal Background for Tough Interviews 183
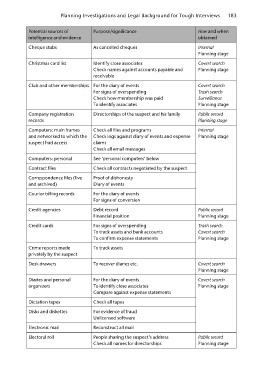
Potential sources of Purpose/significance How and when
intelligence and evidence As cancelled cheques obtained
Internal
Cheque stubs Planning stage
Covert search
Christmas card list Identify close associates Planning stage
Check names against accounts payable and
receivable Covert search
Trash search
Club and other memberships For the diary of events Surveillance
For signs of overspending Planning stage
Check how membership was paid Public record
To identify associates Planning stage
Internal
Company registration Directorships of the suspect and his family Planning stage
records
Public record
Computers: main frames Check all files and programs Planning stage
and networked to which the Check logs against diary of events and expense Trash search
suspect had access claims Covert search
Check all email messages Planning stage
Computers: personal See ‘personal computers’ below Covert search
Planning stage
Contract files Check all contracts negotiated by the suspect Covert search
Planning stage
Correspondence files (live Proof of dishonesty
and archived) Diary of events Public record
Planning stage
Courier billing records For the diary of events
For signs of conversion
Credit agencies Debt record
Financial position
Credit cards For signs of overspending
To track assets and bank accounts
To confirm expense statements
Crime reports made To track assets
privately by the suspect
Desk drawers To recover diaries etc.
Diaries and personal For the diary of events
organizers To identify close associates
Compare against expense statements
Dictation tapes
Disks and diskettes Check all tapes
Electronic mail For evidence of fraud
Electoral roll Unlicensed software
Reconstruct all mail
People sharing the suspect’s address
Check all names for directorships