Page 1 - What is the Workflow for Non-Grant Invoices
P. 1
Workflow for Non-Grant Invoices
What is the Workflow for Non-Grant Invoices?
Overview
Invoicing Workflow is implemented for the four University Business Units (BUs) below. All invoices will be routed to
General Accounts Receivable (GAR). GAR is identified as BI Central in the Workflow process.
ARAFF (Online invoices only. Contract-produced invoices will not be subject to workflow.)
ARDAR
ARGAR
ARSOM
Invoices for other BUs will not be subject to workflow within Compass.
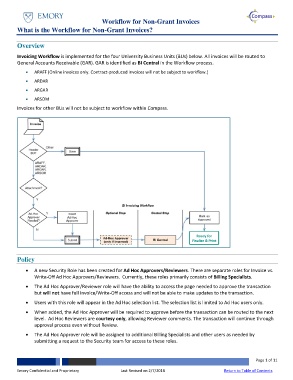
The Invoice cannot be submitted for approval unless
Supporting Documentation has been attached.
Ready for
Finalize & Print
Policy
A new Security Role has been created for Ad Hoc Approvers/Reviewers. There are separate roles for Invoice vs.
Write-Off Ad Hoc Approvers/Reviewers. Currently, these roles primarily consists of Billing Specialists.
The Ad Hoc Approver/Reviewer role will have the ability to access the page needed to approve the transaction
but will not have full Invoice/Write-Off access and will not be able to make updates to the transaction.
Users with this role will appear in the Ad Hoc selection list. The selection list is limited to Ad Hoc users only.
When added, the Ad Hoc Approver will be required to approve before the transaction can be routed to the next
level. Ad Hoc Reviewers are courtesy only, allowing Reviewer comments. The transaction will continue through
approval process even without Review.
The Ad Hoc Approver role will be assigned to additional Billing Specialists and other users as needed by
submitting a request to the Security team for access to these roles.
Page 1 of 11
Emory Confidential and Proprietary Last Revised on 2/7/2018 Return to Table of Contents